-
Security NotificationSecurity Reports22 April, 2022phishing emailA phishing email claiming to be sent from NETVIGATOR. The phishing email alleged that customer's auto payment is failed and the payment information is needed to be updated. Fake hyperlinks are provided in the emails, tricking the recipients into providing their credit card information.26 May, 2021Bogus callA bogus telephone call pretending to be NETVIGATOR staff, advising abnormal situation on the router has been found, their email service needed to be reactivated, abnormal usage on their Internet service has been detected, or that their network or their NETVIGATOR account has been hacked.12 March, 2021phishing emailA phishing email claiming to be sent from NETVIGATOR. The phishing email alleged that customer's auto payment is failed and the payment information is needed to be updated. Fake hyperlinks are provided in the emails, tricking the recipients into providing their credit card information.27 January, 2021Phishing SMSA phishing SMS claiming to be sent from NETVIGATOR. The phishing SMS alleged that the recipients had paid NETVIGATOR monthly fees twice and informed them to follow certain steps for refund.9 November, 2020Bogus websiteBogus online activities purporting to be organised by NETVIGATOR, misleading netizens to answer a few questions and to disclose certain personal information in order to win a prize19 October, 2020Bogus websiteBogus online activities purporting to be organised by NETVIGATOR, misleading netizens to answer a few questions and to disclose certain personal information in order to win a prize19 August, 2020Bogus websiteA bogus online survey purporting to be organised by NETVIGATOR, misleading netizens to answer a few questions and to disclose certain personal information in order to win a prize20 July, 2020Bogus websiteA bogus online customer reward program purporting to be organised by NETVIGATOR, misleading netizens to answer a few questions and to disclose certain personal information in order to win a prize15 July, 2020Bogus callA bogus telephone call pretending to be NETVIGATOR staff, advising customers that abnormal usage on their Internet service has been detected, or that their network or their NETVIGATOR account has been hacked. Thus, misleading to provide certain personal information.28 May, 2020Bogus websiteA bogus online survey purporting to be organised by NETVIGATOR, misleading netizens to disclose their personal information for receiving a prize5 May, 2020Bogus websiteA bogus online customer reward program purporting to be organised by NETVIGATOR, misleading netizens to answer a few questions and to disclose certain personal information in order to win a prize14 April, 2020Bogus websiteA bogus online customer reward program purporting to be organised by NETVIGATOR, misleading netizens to answer a few questions and to disclose certain personal information in order to win a prize22 February, 2020Bogus websiteA bogus online customer reward program purporting to be organised by NETVIGATOR, misleading netizens to answer a few questions and to disclose certain personal information in order to win a prize7 February, 2020Bogus websiteA bogus online customer reward program purporting to be organised by NETVIGATOR, misleading netizens to answer a few questions and to disclose certain personal information in order to win a prize11 Oct, 2019Bogus websiteA bogus online campaign purporting to be organised by NETVIGATOR, misleading netizens to pay for receiving a prize30 Sep, 2019Bogus websiteA bogus online customer reward program purporting to be organised by NETVIGATOR, misleading netizens to answer a few questions and to disclose certain personal information in order to win a prize
-
Beware of phishing emailAn alert from NETVIGATOR: Beware of phishing email
Our attention has been drawn to phishing emails apparently from HKT, NETVIGATOR or My HKT.
Phishing email makes false statements such as suggesting the recipient’s monthly NETVIGATOR subscription remains unpaid, or that his/her mailbox is full. Requests can include supply of credit information, while fake hyperlinks trick recipients into providing their NETVIGATOR login names, passwords or credit card information. Please note that hyperlinks in phishing email and the sender’s actual email address will differ from those used by NETVIGATOR.
Such emails were NOT sent by us. We would never ask for a customer’s credit card information or other personal data via email.
NETVIGATOR Customer Service: custserv@netvigator.comNETVIGATOR’s customer service email address is “NETVIGATOR Customer Service: custserv@netvigator.com” as above. If you receive an email purporting to be from NETVIGATOR, it must carry this address. If it does not, then it is almost certainly bogus. If you receive a suspicious email claiming to be from NETVIGATOR, please do not reply, do not click on the links provided, nor download any attachment. Instead, report it to us at pmaster@netvigator.com. Alternatively, you can contact us via Online Live Chat, or call the consumer service hotline on 1000. We will investigate immediately.
What is phishing email?This is a form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Phishing email usually includes attachments, software or an upgrade program containing a virus or spyware. It can also include a link to a fake website to trick you into divulging information such as account IDs and passwords. A victim’s PC can even be used as a “zombie computer” to attack other users’ devices, with often disastrous consequences.
Destructive powerCybercriminals pose as reputable entities and send email designed to trick users into clicking on a malicious link. The idea is to cheat a user into divulging account IDs, passwords, name, address, telephone number or credit card information – all to be used for fraudulent purposes.
Some cybercriminals use an innocent user’s infected computer to send out phishing emails. Such infections can be caused by a virus, Trojan horse or malware. This often results in a user’s email provider having its server blacklisted, which can cause serious delays in delivery because several days can pass before a blacklisting is reversed.
 How to identify phishing email
How to identify phishing emailPhishing messages are made to look as if they come from a reputable organization and often carry an attractive prospect in the subject field, while others appear to be from a government agency or bank. It is therefore essential to learn how to identify phishing email.
-
1. Pay attention to the recipient’s name
Some phishing emails are sent to groups of people, and most will not include your name.
-
2. Check a hyperlinked website’s layout
Phishing email normally contains a hyperlink to a bogus website that uses a URL and domain name similar to a legitimate entity’s site. A phishing website may include logos or other identifying information taken directly from a genuine website, making it difficult to discern a fake from the real thing. If in doubt, check with the organization concerned.
The URL of phishing website is very similar to the real website's, and the phishing website layout looks almost the same as the authentic one too.
-
-
3. Check a hyperlinked web address
Phishing hyperlinks are normally similar to legitimate URLs. Use of subdomains and misspelled URLs – known as typo squatting – are common tricks, as is homograph spoofing whereby URLs are created using characters to read exactly like a trusted domain. You can simply mouse over a hyperlink to check out its real URL address.
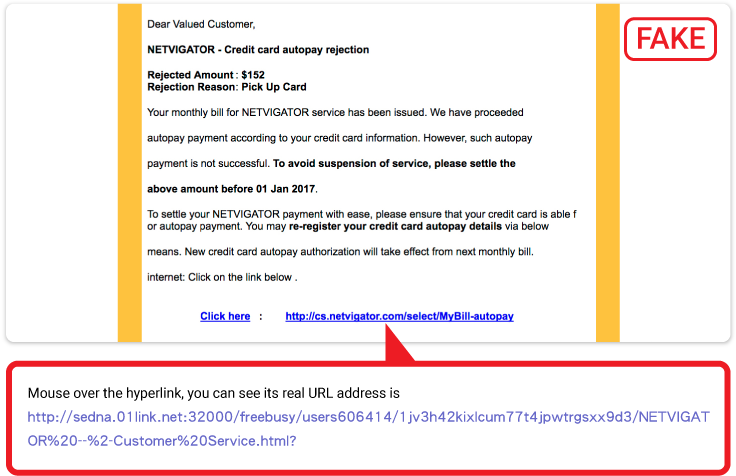
-
4. View an email sender’s name and address
Phishing email purports to be from a well-known entity, but senders’ names and addresses differ from those of legitimate organizations. Simply look at the text inside the < > symbols to check out the actual email address.
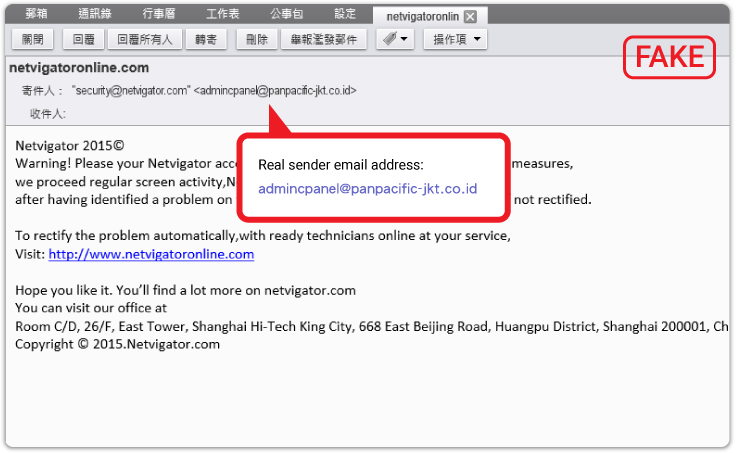
The email above, for example, tells us the sender’s address is security@netvigator.com, but we can see that the sender’s email address is not “netvigator.com” between the < > symbols. This means it is NOT the official email address of NETVIGATOR, so could well be a phishing email.
-
5. Email content containing threatening words
Some phishing emails contain threats or an emergency alert. For example, you could be told your account information is invalid, or your email capacity is almost exhausted, so you are asked to provide credit information, or login to your account via the URL provided.
-
6. Flawed grammar in phishing email content
Most email issued by large companies goes through an editorial quality process, so if an email’s grammar is sub-standard, it could be a phishing attempt.
Prevent phishing emailInstall an anti-virus softwareReliable anti-virus software is designed to detect and deal with most kinds of phishing email, as well as viruses, spyware, malware and Trojans. Such software should be installed on all Internet devices such as mobile phones and tablets.
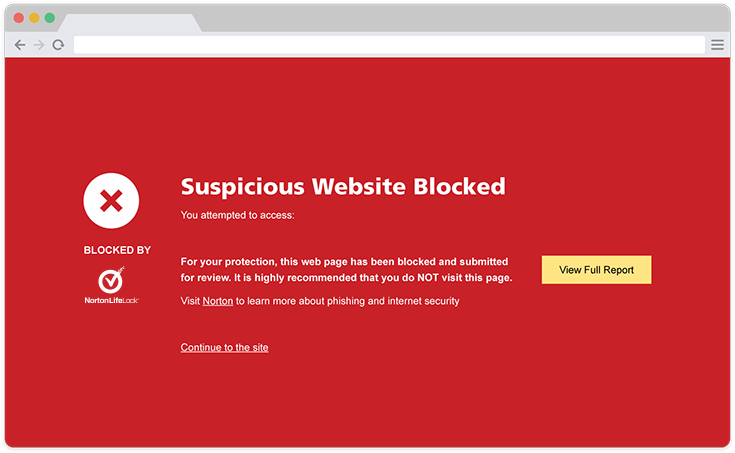
If a user visits a harmful website, Norton Security immediately shields the site and prompts the user to leave.
Select a reliable email providerSome free webmail services do not provide comprehensive protection, so it’s important to use a reliably safe email service in order to reduce the risk of spam and phishing messages being received. A safe email service should provide spam filtering and anti-phishing functionality. Some reputable email services filter malicious email that contains virus-bearing attachments or phishing hyperlinks.
Activate spam-filtering functionalityNETVIGATOR email service verifies a sender’s IP address and domain name. Its “Enhanced Junk Filter” feature aims to block spam and phishing emails. It automatically sends them to spam folders to minimize email-based hacker attacks.
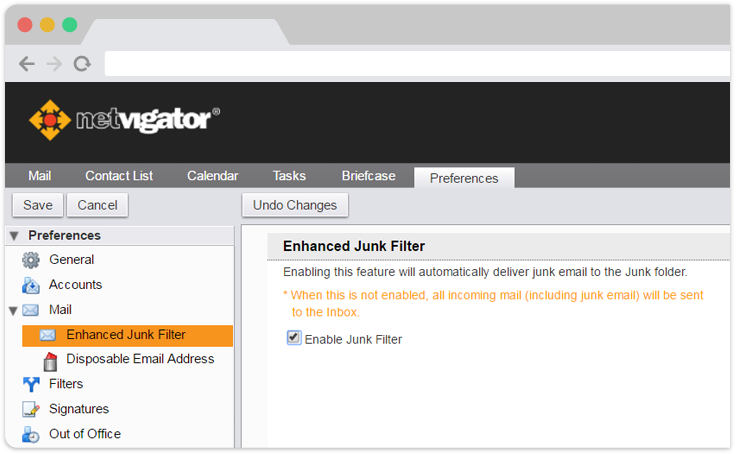
“Enhanced Junk Filter” feature can block spam and phishing emails, automatically sending them to spam folders to reduce email-based hacker attacks.
Use a disposable email addressNETVIGATOR also provides a “disposable email address” feature that allows you to create up to 20 disposable email addresses. This aims to prevent leakage of genuine email addresses and reduces the likelihood of phishing email being received.
Change your email password frequentlyYou should change your email password periodically – and use a different password combination to register for online services. This can reduce the risk of your account being hacked.
Never open suspicious emails or attachmentsIf you suspect you have received a phishing email, do NOT click on any link or attachment. Remember, you can always make a quick call to verify authenticity. You can also seek assistance from your email service provider.
And if you receive an email asking you to verify your personal or account information – such as by revealing passwords, online banking login information, or credit card numbers – resist any temptation to comply.
-
 Phishing email example
Phishing email example
-
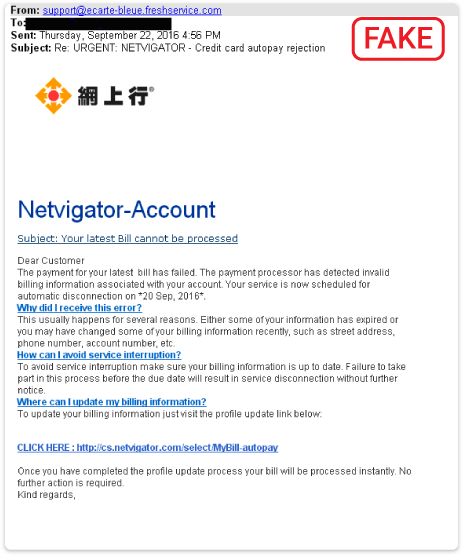 Phishing email example
Phishing email example
-
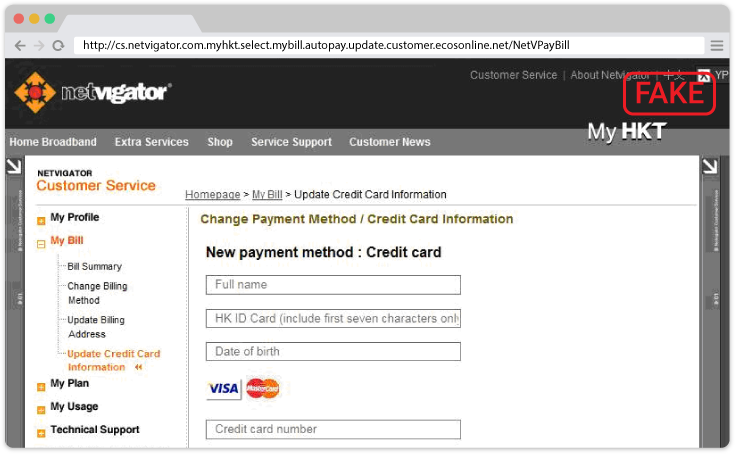 Phishing email example
Phishing email example
Click here to find out more information on Email Scam.
Please contact us if you suspect someone posing as NETVIGATOR has sent you email. Simply report it to pmaster@netvigator.com and we will act immediately. You can also contact us via the online Live Chat service, or call the PCCW Consumer Service Hotline on 1000.
-
-
Beware of ransomwareAn alert from NETVIGATOR: Beware of ransomware
Cybercriminals make money by using viruses to pose threats to systems and files – and ransomware has become one of the most common such scams. A characteristic is that it does not damage a victim’s computer data immediately. Instead, it encrypts data using high-spec methods and denies access to the owner. A ransom is demanded if the user wants access to his/her own data.
Bank-level encryptionCommon ransomware employs bank-level encryption methods similar to those used in online transactions. Encryption and decryption keys are different, so even though the encryption key might be found on a victim’s computer, decryption cannot be guaranteed. A key could be as long as 1024 or even 2048 bits, which means decryption could take up to a million years to calculate.
 Covert infection
Covert infectionEarlier computer viruses required users to download malicious files, but simply visiting a malicious website is enough to do damage these days. Ransomware such as WannaCry exploited a Windows security bug and spread itself into un-patched Windows computers connected on the same network. The fact was, many users were not accustomed to installing security patches or activating Windows updates, and this increased the severity and scale of the damage.
Botnets and botsOther types of cyber attacks are occurring in the background with hardly anyone noticing. Some attacks aim to recruit victims’ computers as bots in a botnet for future attacks. These can involve congesting networks, or mining bitcoins.
 Taking care of Mac and Android devices
Taking care of Mac and Android devicesMac is perceived to be secure, but has been found infected by MacRansom ransomware. Although scale of attack has been limited, it is worth noting its significance. Mobile payment and banking are getting more popular, so criminals are starting to target mobile platforms. The incidence of malicious apps infecting the Android operating system is increasing. These malicious apps not only lock up the screen and encrypt user files – some even reset the screen lock PIN, open specific websites via the browser, steal message contents and contact information, and switch Wi-Fi and mobile data on/off, as well as track a user’s location – all constituting a significant threat. Malicious apps are also able to infect iOS and NAS devices, so users should pay attention to all connected devices.
 Better practices
Better practicesUsers wishing to protect their devices from cyber attacks should follow best practices, such as:
- Backup regularly and keep an offline copy in a safe place, preventing exposure to malicious apps
- Install/update OS and software security patches regularly
- Install and update antivirus software regularly
- Perform full computer scans regularly to detect and prevent malicious app attacks
- Disable or restrict a computer system’s unnecessary features and services
- Do not open suspicious emails or download attachments from them
- Do not visit suspicious websites or download files from such websites
Do not skip updates for your anti-virus software or operating system, as the time you save could turn out to be far more expensive than you imagined!
Click here to find out more information on "No More Ransom".
-
Other Internet Safety and Technology Crime information
Security Corner
It’s not enough just to be alert to online security issues – we also need to install comprehensive anti-virus software and use a reliable email provider to ensure important information is kept safe.
Security Corner


